Rombertik - Malware
A group of security researchers working for the US Cisco got their hands on a particularly virulent malware, dubbed Rombertik. In addition to spying on the machine on which it is installed, it can know if it is spotted and address the hard drive in order to make the system unusable.
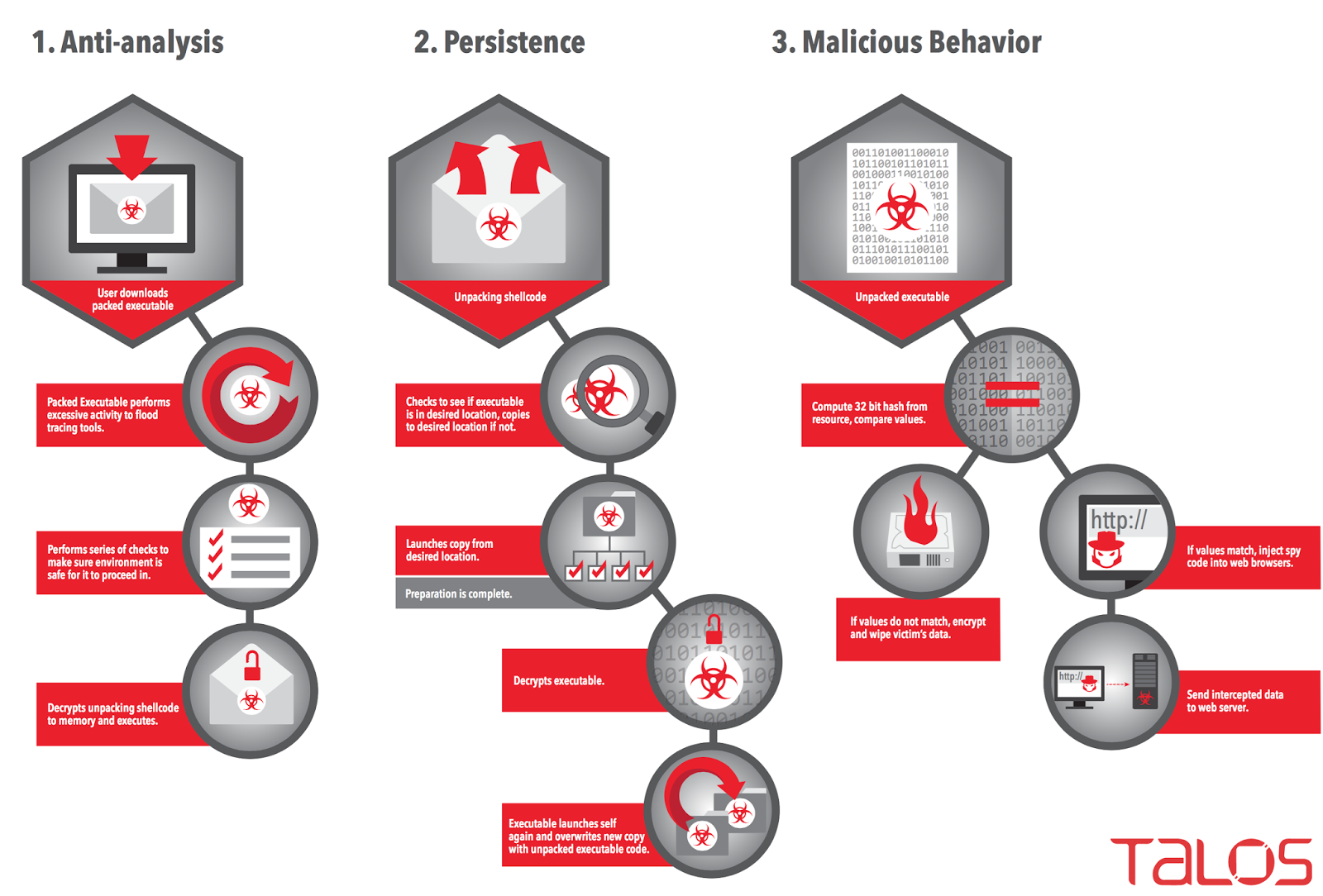
Initially, nothing distinguishes Rombertik other more common malware. It weaves through mailboxes, traditional weapons are spam and phishing inevitably being the privileged propagation vectors. But once the attachment opened by the user (which may take the form of a PDF file, or a compressed file), it is the drama.
For this formidable malware has several strings to his bow. Naturally, it will try to recover sensitive data by monitoring what you type on the keyboard and then send this information to the authors of this malicious code. But that is not the feature of this program.
Once installed, your data and your system are lost
The latter is characterized rather by its ability to protect themselves and the scorched earth policy that is his. After the code is executed, the malware will first check if it operates within a sandbox, a sort of virtual system intended to prevent the spread.
When that routine monitoring is carried out, it will deploy and verify that it is not the subject of a brief analysis. If that is the case, it attacks the MBR of the machine storage medium, so as to make the system inoperative. If it fails, it will get down to encrypt user files and then restart the machine, which will never be able to display Windows again. Why? Because Rombertik will have taken care to execute code before launching the operating system so as to create an infinite loop.
If the malware escapes the memory analysis, the PC prevents the damage. But they still arrive when a virus has undertaken a scan of the machine. Scan which will also slowed by a staggering amount of information will produce Rombertik. This malware is designed to fool the scan engines, since it is composed largely unnecessary code and dummy data.
Finally, Rombertik is designed to lure antivirus and win enough time to collect as much data. Once compromised, he leaves nothing in its path.
An MBR is recovering, and a backup of your data so you can restore your system as it was before the arrival of this monster. But the easiest is probably to avoid clicking on an attachment placed in an email that you do not know the sender.


0 comments :
Post a Comment